|
| 1 | +# Edge 2 - 200 points |
| 2 | + |
| 3 | +Last time we screwed up. But we've learned our lesson. |
| 4 | + |
| 5 | +### Solution |
| 6 | +###### Writeup by Valar Dragon |
| 7 | + |
| 8 | +Beginning with the same procedure as Edge 1, navigate to `/.git` |
| 9 | + |
| 10 | +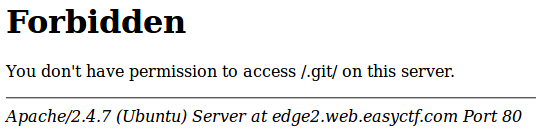 |
| 11 | + |
| 12 | +So the directory exists, but they've blocked directory listing! |
| 13 | + |
| 14 | +So were going to do the same attack at last time, but instead of doing a recursive download, we will have to download the files manually. |
| 15 | +There is going to be a lot of overlap between the Edge 1 and Edge 2 .git directories, since they are both cloned from the same project. |
| 16 | +So lets start by copying everything from Edge 1 into an Edge 2 directory. |
| 17 | + |
| 18 | +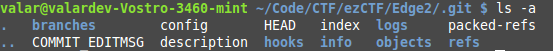 |
| 19 | + |
| 20 | +So we need to replace all the `logs, refs, COMMIT_EDITMSG, HEAD, index, and then finally the objects`. |
| 21 | + |
| 22 | +Updating everything but objects is pretty straightforward. |
| 23 | + |
| 24 | +Just navigate to the `/logs/HEAD` and `logs/refs/heads/master` to ge those files, and likewise for the rest of the files. |
| 25 | + |
| 26 | +Now we can take the git log! |
| 27 | + |
| 28 | +``` html |
| 29 | +$ git log |
| 30 | +commit a48ee6d6ca840b9130fbaa73bbf55e9e730e4cfd |
| 31 | +Author: Michael <michael@easyctf.com> |
| 32 | +Date: Mon Mar 13 07:32:12 2017 +0000 |
| 33 | + |
| 34 | + Prevent directory listing. |
| 35 | + |
| 36 | +commit 6b4131bb3b84e9446218359414d636bda782d097 |
| 37 | +Author: Michael <michael@easyctf.com> |
| 38 | +Date: Mon Mar 13 07:32:10 2017 +0000 |
| 39 | + |
| 40 | + Whoops! Remove flag. |
| 41 | + |
| 42 | +commit 26e35470d38c4d6815bc4426a862d5399f04865c |
| 43 | +Author: Michael <michael@easyctf.com> |
| 44 | +Date: Mon Mar 13 07:32:09 2017 +0000 |
| 45 | + |
| 46 | + Initial. |
| 47 | + |
| 48 | +commit 15ca375e54f056a576905b41a417b413c57df6eb |
| 49 | +Author: Fernando <fermayo@gmail.com> |
| 50 | +Date: Sat Dec 14 12:50:09 2013 -0300 |
| 51 | + |
| 52 | + initial version |
| 53 | + |
| 54 | +``` |
| 55 | + |
| 56 | +Now we have to update the objects directory. Here is the format of the directory: |
| 57 | + |
| 58 | +``` |
| 59 | +$ ls objects |
| 60 | +09 15 3e 61 6a 7b 8a 96 9e a7 b9 bf e0 ee pack |
| 61 | +14 37 5d 64 71 7c 94 9b a1 af bd d1 ed info |
| 62 | +$ ls objects/15 |
| 63 | +ca375e54f056a576905b41a417b413c57df6eb |
| 64 | +$ cat objects/15/ca375e54f056a576905b41a417b413c57df6eb |
| 65 | +x��jC!���)�@ˮ�������cյ����)��yW�� |
| 66 | +
|
| 67 | + L��ե��Et��|�4N�E��H�7�����E{�Uw�җ�8Q >��d���>W\A����[t\�Q�\�c�o��{��Rd6�������J�]5�-���v� �@���[�n�j�����d>���3�D� |
| 68 | +``` |
| 69 | +Each folder in objects is the first 2 characters of the SHA1, and the names of the files are the rest of the SHA1. |
| 70 | +The contents of each file is not ascii. |
| 71 | +Git objects are actually zlib compressed to save space, so |
| 72 | +``` html |
| 73 | +$ zlib-flate -uncompress < objects/15/ca375e54f056a576905b41a417b413c57df6eb commit 220tree 7b456b0125e74b44d1147182019c704c53132013 |
| 74 | +parent 8ac4f76df2ce8db696d75f5f146f4047a315af22 |
| 75 | +author Fernando <fermayo@gmail.com> 1387036209 -0300 |
| 76 | +committer Fernando <fermayo@gmail.com> 1387036209 -0300 |
| 77 | + |
| 78 | +initial version |
| 79 | + |
| 80 | +``` |
| 81 | +So each commit has a git object with files it edited! |
| 82 | +So we are going to need to checkout the commit: |
| 83 | +``` html |
| 84 | +commit 26e35470d38c4d6815bc4426a862d5399f04865c |
| 85 | +Author: Michael <michael@easyctf.com> |
| 86 | +Date: Mon Mar 13 07:32:09 2017 +0000 |
| 87 | + |
| 88 | + Initial. |
| 89 | +``` |
| 90 | +So |
| 91 | + |
| 92 | +``` html |
| 93 | +$ zlib-flate -uncompress < objects/26/e35470d38c4d6815bc4426a862d5399f04865c |
| 94 | +commit 215tree 323240a3983045cdc0dec2e88c1358e7998f2e39 |
| 95 | +parent 15ca375e54f056a576905b41a417b413c57df6eb |
| 96 | +author Michael <michael@easyctf.com> 1489390329 +0000 |
| 97 | +committer Michael <michael@easyctf.com> 1489390329 +0000 |
| 98 | + |
| 99 | +Initial. |
| 100 | + |
| 101 | +``` |
| 102 | +Then get the file `objects/32/3240a3983045cdc0dec2e88c1358e7998f2e39` |
| 103 | +I did the same for every other commit. |
| 104 | + |
| 105 | +Then `git checkout 26e35470d38c4d6815bc4426a862d5399f04865c` |
| 106 | +and then theres a flag.txt in the main dir! |
| 107 | +``` |
| 108 | +$ cat flag.txt |
| 109 | +easyctf{hiding_the_problem_doesn't_mean_it's_gone!} |
| 110 | +
|
| 111 | +``` |
| 112 | + |
| 113 | + |
| 114 | +### External Writeups |
| 115 | + |
| 116 | +* [https://github.com/HackThisCode/CTF-Writeups/blob/master/2017/EasyCTF/Edge%202/README.md](https://github.com/HackThisCode/CTF-Writeups/blob/master/2017/EasyCTF/Edge%202/README.md) |
0 commit comments