You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
HTTPS callback URLs provide enhanced security compared to custom URL schemes. They work with Android App Links and iOS Universal Links to prevent URL scheme hijacking:
Copy file name to clipboardExpand all lines: FAQ.md
+1-1
Original file line number
Diff line number
Diff line change
@@ -261,4 +261,4 @@ If you don't need SSO, consider using `ephemeral sessions` or `SFSafariViewContr
261
261
262
262
## 9. How can I prevent the autogenerated redirect_uri from breaking if the applicationId has mixed cases or special characters in it on Android ?
263
263
264
-
It is recommended to have your applicationId in lower case without special characters to prevent any mismatch with the generated redirect_uri. But in the scenario where you require your applicationId to be of mixed case, to avoid any mismatch , the user can pass a `redirectUri`whihc matches the one provided in the manage dashboard as part of the `AgentLoginOptions` property.
264
+
It is recommended to have your applicationId in lower case without special characters to prevent any mismatch with the generated redirect_uri. But in the scenario where you require your applicationId to be of mixed case, to avoid any mismatch , the user can pass a `redirectUri`which matches the one provided in the manage dashboard as part of the `AgentLoginOptions` property.
Copy file name to clipboardExpand all lines: README.md
+95-6
Original file line number
Diff line number
Diff line change
@@ -103,8 +103,6 @@ Take note of this value as you'll be requiring it to define the callback URLs be
103
103
104
104
> For more info please read the [React Native docs](https://facebook.github.io/react-native/docs/linking.html).
105
105
106
-
> Whenever possible, Auth0 recommends using `https` scheme with [Android App Links](https://auth0.com/docs/applications/enable-android-app-links) as a secure way to link directly to content within your app. Custom URL schemes can be subject to [client impersonation attacks](https://datatracker.ietf.org/doc/html/rfc8252#section-8.6).
107
-
108
106
##### Skipping the Web Authentication setup
109
107
110
108
If you don't plan to use Web Authentication, you will notice that the compiler will still prompt you to provide the `manifestPlaceholders` values, since the `RedirectActivity` included in this library will require them, and the Gradle tasks won't be able to run without them.
@@ -213,21 +211,112 @@ Go to the [Auth0 Dashboard](https://manage.auth0.com/#/applications), select you
213
211
214
212
If in addition you plan to use the log out method, you must also add these URLs to the **Allowed Logout URLs**.
215
213
214
+
> [!NOTE]
215
+
> Whenever possible, Auth0 recommends using [Android App Links](https://developer.android.com/training/app-links) and [Apple Universal Links](https://developer.apple.com/documentation/xcode/allowing-apps-and-websites-to-link-to-your-content) for your callback and logout URLs. Custom URL schemes can be subject to [client impersonation attacks](https://datatracker.ietf.org/doc/html/rfc8252#section-8.6).
216
+
>
217
+
> 💡 If your Android app is using [product flavors](https://developer.android.com/studio/build/build-variants#product-flavors), you might need to specify different manifest placeholders for each flavor.
> Replace {YOUR_APP_PACKAGE_NAME} and {YOUR_AUTH0_DOMAIN} with your actual application package name and Auth0 domain. Ensure that {YOUR_APP_PACKAGE_NAME} is all lowercase.
234
+
235
+
To enable App Links, set the `auth0Scheme` to `https` in your `build.gradle` file.
> Make sure to replace {YOUR_APP_PACKAGE_NAME} and {AUTH0_DOMAIN} with the actual values for your application. The {YOUR_APP_PACKAGE_NAME} value provided should be all lower case.
245
+
This configuration ensures that your app uses https for the callback URL scheme, which is required for Android App Links.
246
+
247
+
#### Enable Android App Links Support
248
+
249
+
[Android App Links](https://developer.android.com/training/app-links) allow an application to designate itself as the default handler of a given type of link. For example, clicking a URL in an email would open the link in the designated application. This guide will show you how to enable Android App links support for your Auth0-registered application using Auth0's Dashboard.
250
+
251
+
1. Go to [Auth0 Dashboard > Applications > Applications](https://manage.auth0.com/#/applications), and select the name of the application to view.
252
+
253
+
2. Scroll to the bottom of the Settings page, and select **Show Advanced Settings**.
254
+
3. Select Device Settings, provide the [App Package Name and](https://developer.android.com/studio/build/application-id) the SHA256 fingerprints of your app’s signing certificate for your Android application, and select Save Changes.
255
+

256
+
257
+
> You can use the following command to generate the fingerprint using the Java keytool in your terminal: `keytool -list -v -keystore my-release-key.keystore`
258
+
259
+
To learn more about signing certificates, see Android's [Sign Your App](https://developer.android.com/studio/publish/app-signing.html) developer documentation.
> Make sure to replace {PRODUCT_BUNDLE_IDENTIFIER} and {AUTH0_DOMAIN} with the actual values for your application. The {PRODUCT_BUNDLE_IDENTIFIER} value provided should be all lower case.
> Replace `{PRODUCT_BUNDLE_IDENTIFIER}` and `{YOUR_AUTH0_DOMAIN}` with your actual product bundle identifier and Auth0 domain. Ensure that {PRODUCT_BUNDLE_IDENTIFIER} is all lowercase.
276
+
277
+
#### Configure an associated domain for iOS
278
+
279
+
> [!IMPORTANT]
280
+
> This step requires a paid Apple Developer account. It is needed to use Universal Links as callback and logout URLs.
281
+
> Skip this step to use a custom URL scheme instead.
282
+
283
+
##### Configure the Team ID and bundle identifier
284
+
285
+
Scroll to the end of the settings page of your Auth0 application and open **Advanced Settings > Device Settings**. In the **iOS** section, set **Team ID** to your [Apple Team ID](https://developer.apple.com/help/account/manage-your-team/locate-your-team-id/), and **App ID** to your app's bundle identifier.
286
+
287
+
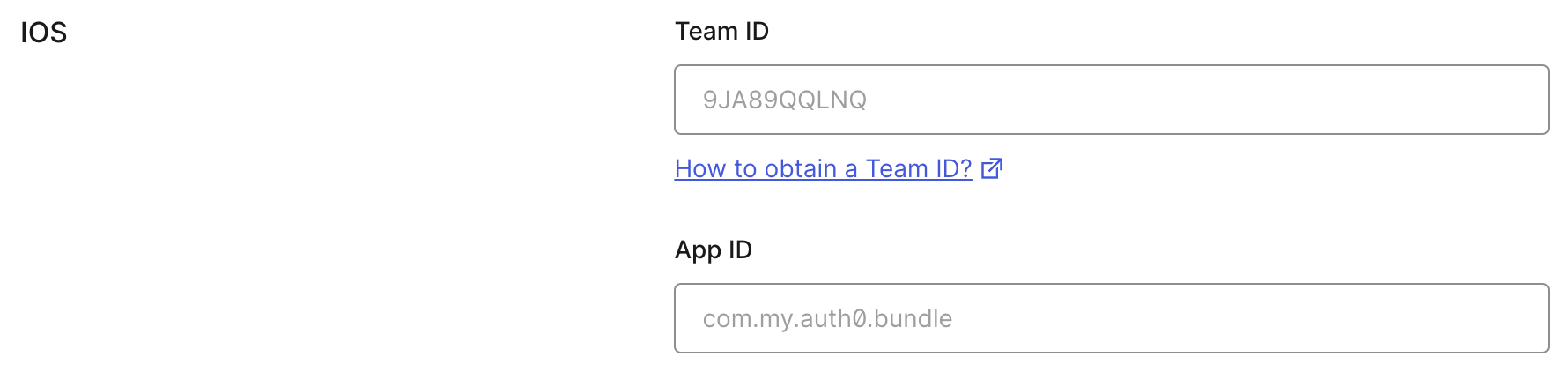
288
+
289
+
This will add your app to your Auth0 tenant's `apple-app-site-association` file.
290
+
291
+
##### Add the associated domain capability
292
+
293
+
In Xcode, go to the **Signing and Capabilities**[tab](https://developer.apple.com/documentation/xcode/adding-capabilities-to-your-app#Add-a-capability) of your app's target settings, and press the **+ Capability** button. Then select **Associated Domains**.
294
+
295
+
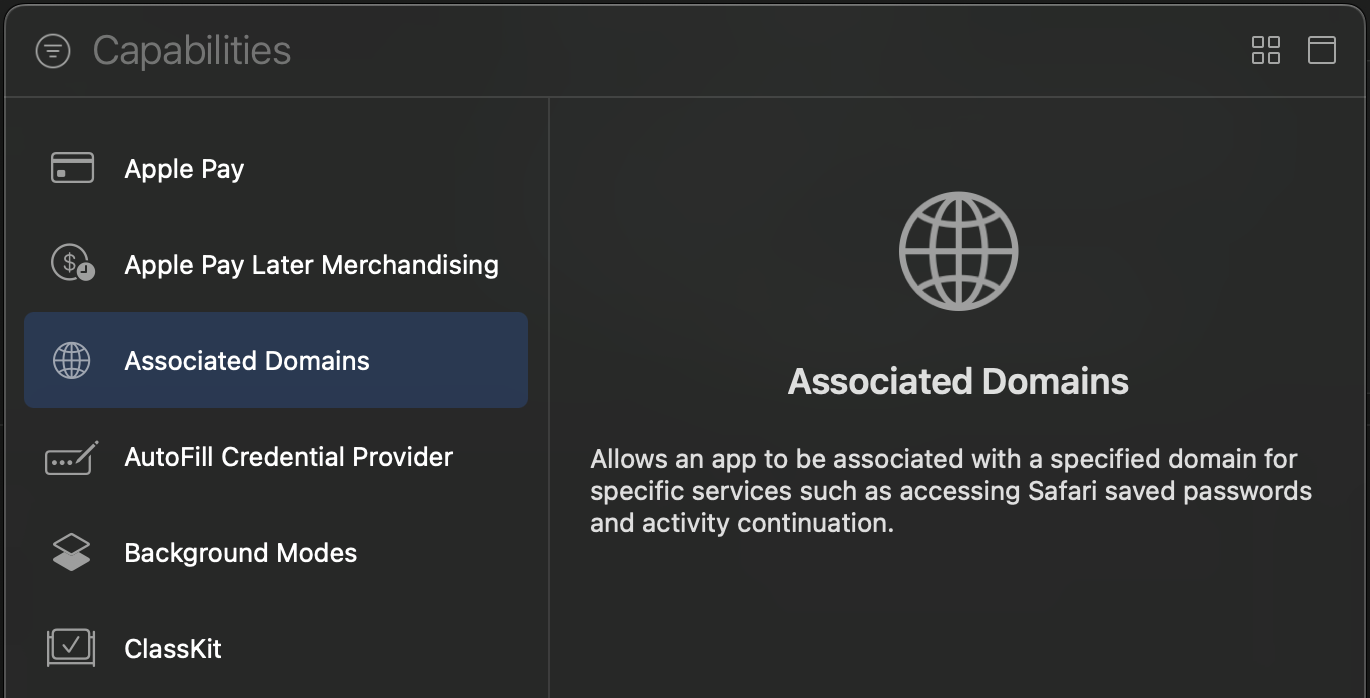
296
+
297
+
Next, add the following [entry](https://developer.apple.com/documentation/xcode/configuring-an-associated-domain#Define-a-service-and-its-associated-domain) under **Associated Domains**:
298
+
299
+
```text
300
+
webcredentials:YOUR_AUTH0_DOMAIN
301
+
```
302
+
303
+
<details>
304
+
<summary>Example</summary>
305
+
306
+
If your Auth0 Domain were `example.us.auth0.com`, then this value would be:
307
+
308
+
```text
309
+
webcredentials:example.us.auth0.com
310
+
```
311
+
312
+
</details>
313
+
314
+
If you have a [custom domain](https://auth0.com/docs/customize/custom-domains), replace `YOUR_AUTH0_DOMAIN` with your custom domain.
315
+
316
+
> [!NOTE]
317
+
> For the associated domain to work, your app must be signed with your team certificate **even when building for the iOS simulator**. Make sure you are using the Apple Team whose Team ID is configured in the settings page of your Auth0 application.
318
+
319
+
Refer to the example of [Using custom scheme for web authentication redirection](https://github.com/auth0/react-native-auth0/blob/master/EXAMPLES.md#using-custom-scheme-for-web-authentication-redirection)
0 commit comments