Authentication OpenID Connect
!! This file is generated by oca-gen-addon-readme !! !! changes will be overwritten. !! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! -!! source digest: sha256:bdea2939597996bddfbd2c7949c8da2ad701b61203c3fd62c0c640bb5721eaf1 +!! source digest: sha256:a54c4126f9873d2af17b9228f9afa844806a2541b42dc7945ec41be08379a915 !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! --> -This module allows users to login through an OpenID Connect provider using the -authorization code flow or implicit flow.
-Note the implicit flow is not recommended because it exposes access tokens to -the browser and in http logs.
+This module allows users to login through an OpenID Connect provider +using the authorization code flow or implicit flow.
+Note the implicit flow is not recommended because it exposes access +tokens to the browser and in http logs.
Table of contents
-
@@ -402,29 +402,32 @@
Authentication OpenID Connect
Installation
-This module depends on the python-jose -library, not to be confused with jose which is also available on PyPI.
+This module depends on the +python-jose library, not to +be confused with jose which is also available on PyPI.
Configuration
Setup for Microsoft Azure
Example configuration with OpenID Connect authorization code flow.
--
-
- # configure a new web application in Azure with OpenID and code flow (see -
- the provider documentation) -
- # in this application the redirect url must be be “<url of your -
- server>/auth_oauth/signin” and of course this URL should be reachable from -Azure -
- # create a new authentication provider in Odoo with the following -
- parameters (see the portal documentation -for more information): -
 -
- -
-Single tenant provider limits the access to user of your tenant, -while Multitenants allow access for all AzureAD users, so user of foreign companies can use their AzureAD login -without an guest account.
+-
+
- configure a new web application in Azure with OpenID and code flow +(see the provider +documentation)) +
- in this application the redirect url must be be “<url of your +server>/auth_oauth/signin” and of course this URL should be reachable +from Azure +
- create a new authentication provider in Odoo with the following +parameters (see the portal +documentation +for more information): +
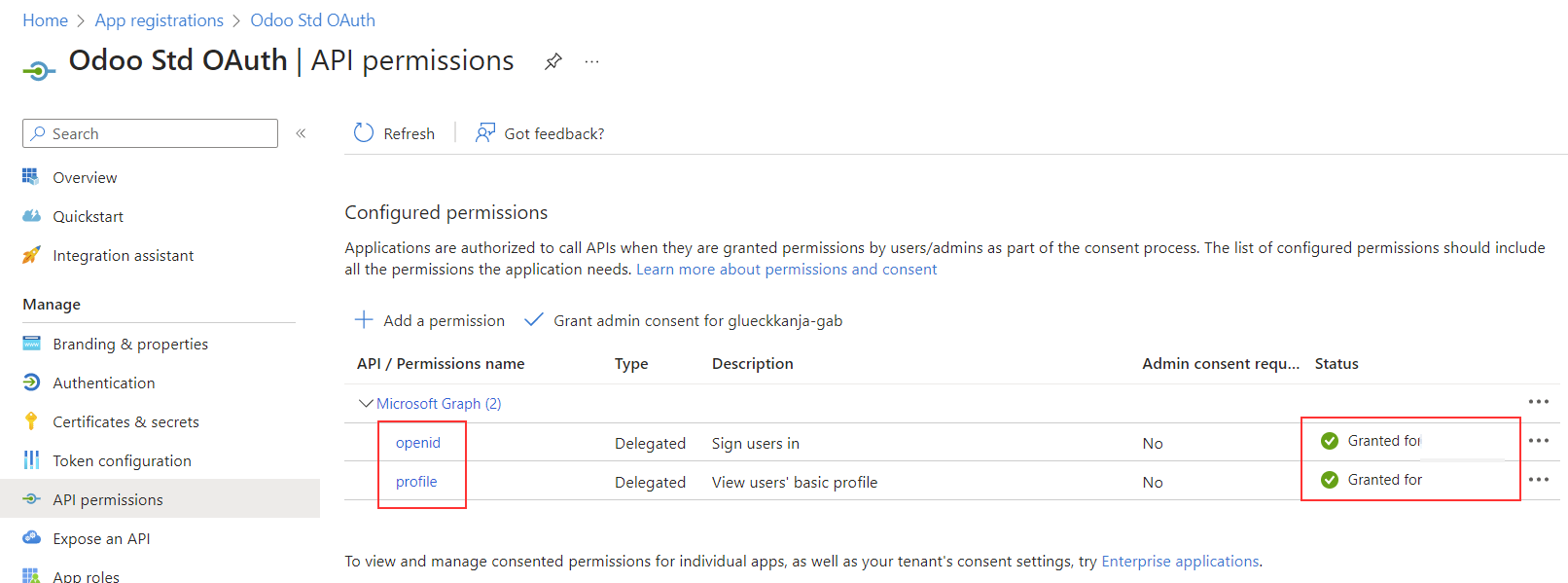
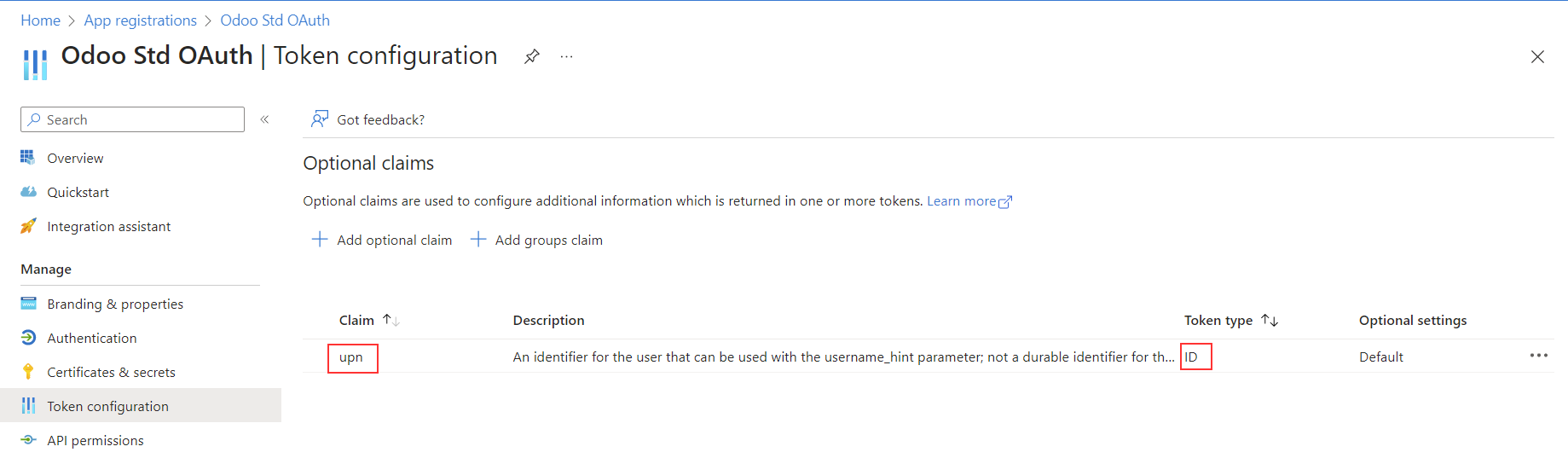
Single tenant provider limits the access to user of your tenant, while +Multitenants allow access for all AzureAD users, so user of foreign +companies can use their AzureAD login without an guest account.
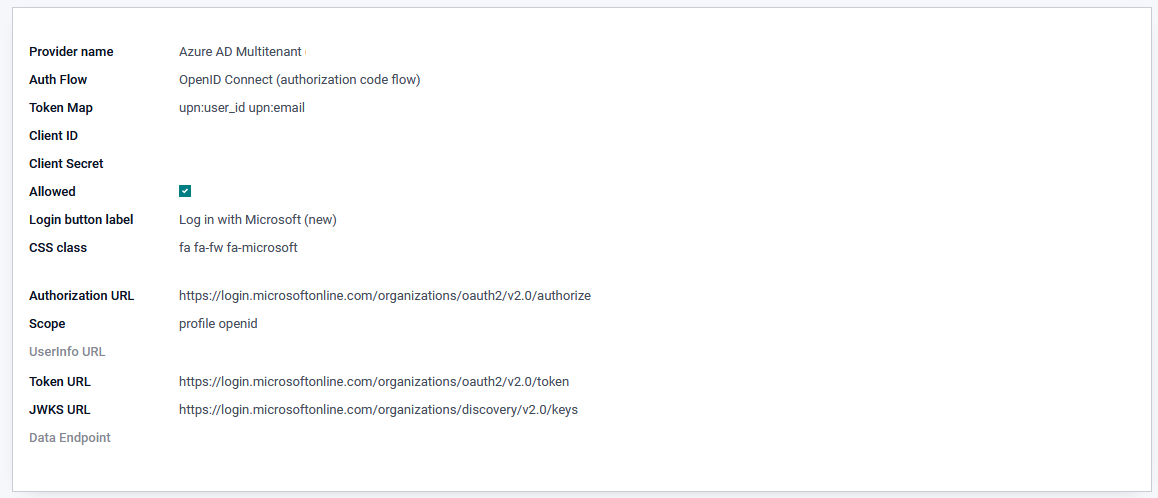
- Provider Name: Azure AD Single Tenant
- Client ID: Application (client) id @@ -439,32 +442,38 @@
- replace {tenant_id} in urls with your Azure tenant id
Setup for Microsoft Azure
Allowed: yes +
+
Setup for Keycloak
Example configuration with OpenID Connect authorization code flow.
In Keycloak:
-# configure a new Client -# make sure Authorization Code Flow is Enabled. -# configure the client Access Type as “confidential” and take note of the client secret in the Credentials tab -# configure the redirect url to be “<url of your server>/auth_oauth/signin”
+-
+
- configure a new Client +
- make sure Authorization Code Flow is Enabled. +
- configure the client Access Type as “confidential” and take note of +the client secret in the Credentials tab +
- configure the redirect url to be “<url of your +server>/auth_oauth/signin” +
In Odoo, create a new Oauth Provider with the following parameters:
-
-
- Provider name: Keycloak (or any name you like that identify your keycloak -provider) +
- Provider name: Keycloak (or any name you like that identify your +keycloak provider)
- Auth Flow: OpenID Connect (authorization code flow) -
- Client ID: the same Client ID you entered when configuring the client in Keycloak +
- Client ID: the same Client ID you entered when configuring the client +in Keycloak
- Client Secret: found in keycloak on the client Credentials tab
- Allowed: yes -
- Body: the link text to appear on the login page, such as Login with Keycloak +
- Body: the link text to appear on the login page, such as Login with +Keycloak
- Scope: openid email
- Authentication URL: The “authorization_endpoint” URL found in the OpenID Endpoint Configuration of your Keycloak realm -
- Token URL: The “token_endpoint” URL found in the -OpenID Endpoint Configuration of your Keycloak realm -
- JWKS URL: The “jwks_uri” URL found in the -OpenID Endpoint Configuration of your Keycloak realm +
- Token URL: The “token_endpoint” URL found in the OpenID Endpoint +Configuration of your Keycloak realm +
- JWKS URL: The “jwks_uri” URL found in the OpenID Endpoint +Configuration of your Keycloak realm
Usage
Known issues / Roadmap
-
-
- When going to the login screen, check for a existing token and do a direct login without the clicking on the SSO link -
- When doing a logout an extra option to also logout at the SSO provider. +
- When going to the login screen, check for a existing token and do a +direct login without the clicking on the SSO link +
- When doing a logout an extra option to also logout at the SSO +provider.