⚠️ Important Security NoticeThis tool is intended for authorized security testing only. Using this tool without explicit permission is illegal and could result in serious legal consequences.
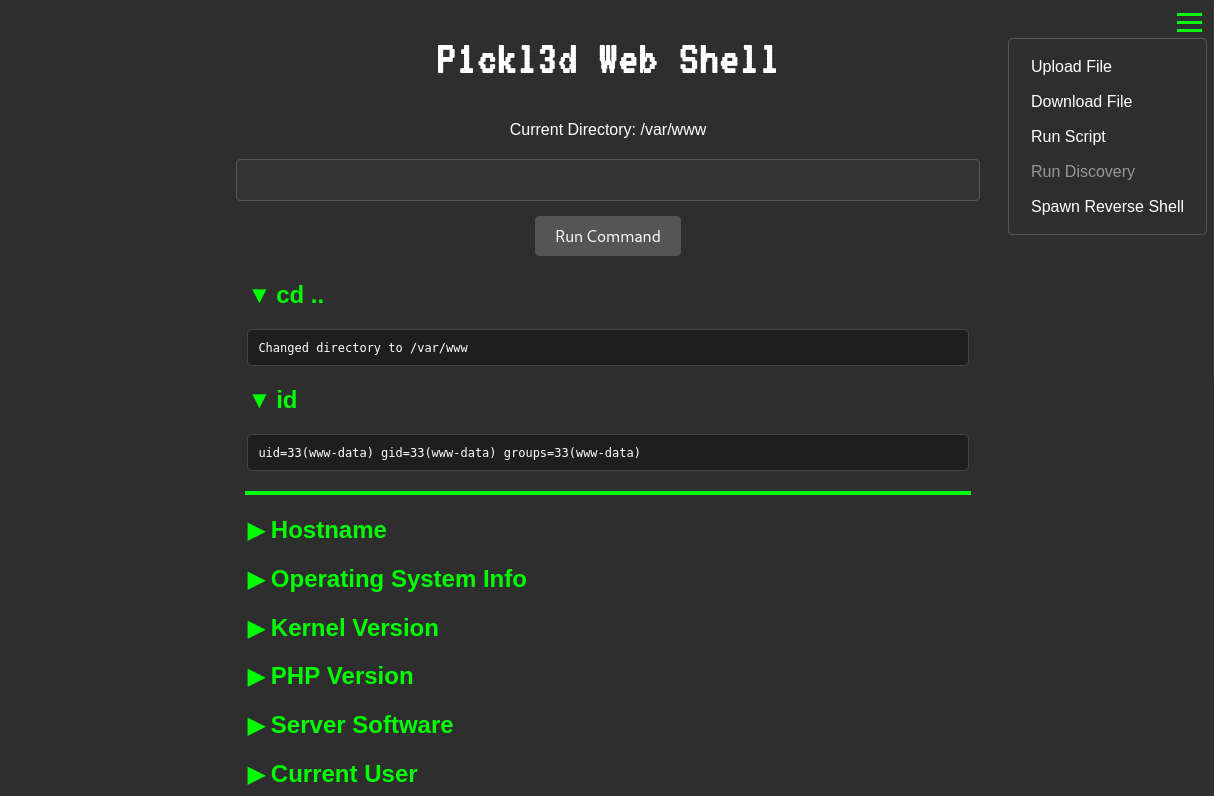
In the realm of cybersecurity and penetration testing, having the right tools is crucial for thorough security assessments. The P1ckl3d Web Shell is an advanced tool designed specifically for security professionals conducting authorized penetration testing.
| Feature | Description |
|---|---|
| 🔄 Dynamic Command Execution | Execute real-time shell commands, maintain history, and avoid page reloads |
| 📁 File Management | Seamless file uploads, directory navigation, and file downloads |
| 🔍 System Information Gathering | Retrieve OS details, network configurations, user info, and security settings |
| 🌐 Network Reconnaissance | Gather details about running processes, services, and open ports |
| 🔑 User Privilege Escalation Analysis | Identify potential privilege escalation vectors |
- A web server with PHP support
- Proper authorization to conduct security testing
- Download the
P1ckl3d-Web-Shell.phpfile from the repository:git clone https://github.com/RootShelll/P1ckl3d-Web-Shell.git cd P1ckl3d-Web-Shell - Identify a suitable upload point on the target system.
- Upload the file through the identified vulnerability.
- Access the web shell through the uploaded URL.
# Execute system commands
command> ls -la
# Change directory
command> cd /var/www
# View file contents
command> cat config.php- Enumerate Running Processes:
ps aux - Check Open Ports:
netstat -tulnp - Retrieve User Information:
whoami && id
✔️ Always maintain detailed logs of your testing activities
✔️ Remove the web shell immediately after testing
✔️ Use secure connections when possible
✔️ Follow the target organization's security testing guidelines
| Issue | Solution |
|---|---|
| Permission Denied | Check file permissions and user context |
| Upload Failed | Verify file size limits and server configurations |
| Connection Issues | Check network connectivity and firewall rules |
This tool is intended strictly for ethical hacking and penetration testing within legal boundaries. The authors and contributors do not take responsibility for misuse or illegal activities related to this software.
For any queries, contributions, or issues, reach out via:
📧 Email: security@R00t-shell.com
💬 Discord: Join our community
🐙 GitHub Issues: Report a bug